Cruise to Cloud Native: Chapter 3 Bringing your team on board into your cloud native journey
Slide 1

Slide 2
Stuti Desphande Solutions Architect at AWS Daniel Maher Technical Evangelist at Datadog @phrawzty Ara Pulido Technical Evangelist at Datadog @arapulido
Slide 3

Cruise to Cloud Native in 3 episodes Episode 1: From bare-metal to AWS (7 May) Episode 2: Getting more from advanced services (16 May) Episode 3: Bringing your company onboard! (Today)
Slide 4

Top migration challenges we hear from customers “We see challenges with existing software contracts, license portability, and vendor willingness to price reasonably during the move of dozens/hundreds of vendors” “We want to evaluate and onboard new software vendors during migration” “We want to bring on-premises governance controls to cloud apps” “We need to drive culture change beyond IT as we transform our businesses to digital and from on-premises to cloud” © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 4
Slide 5
Culture Practices Tools © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 5
Slide 6
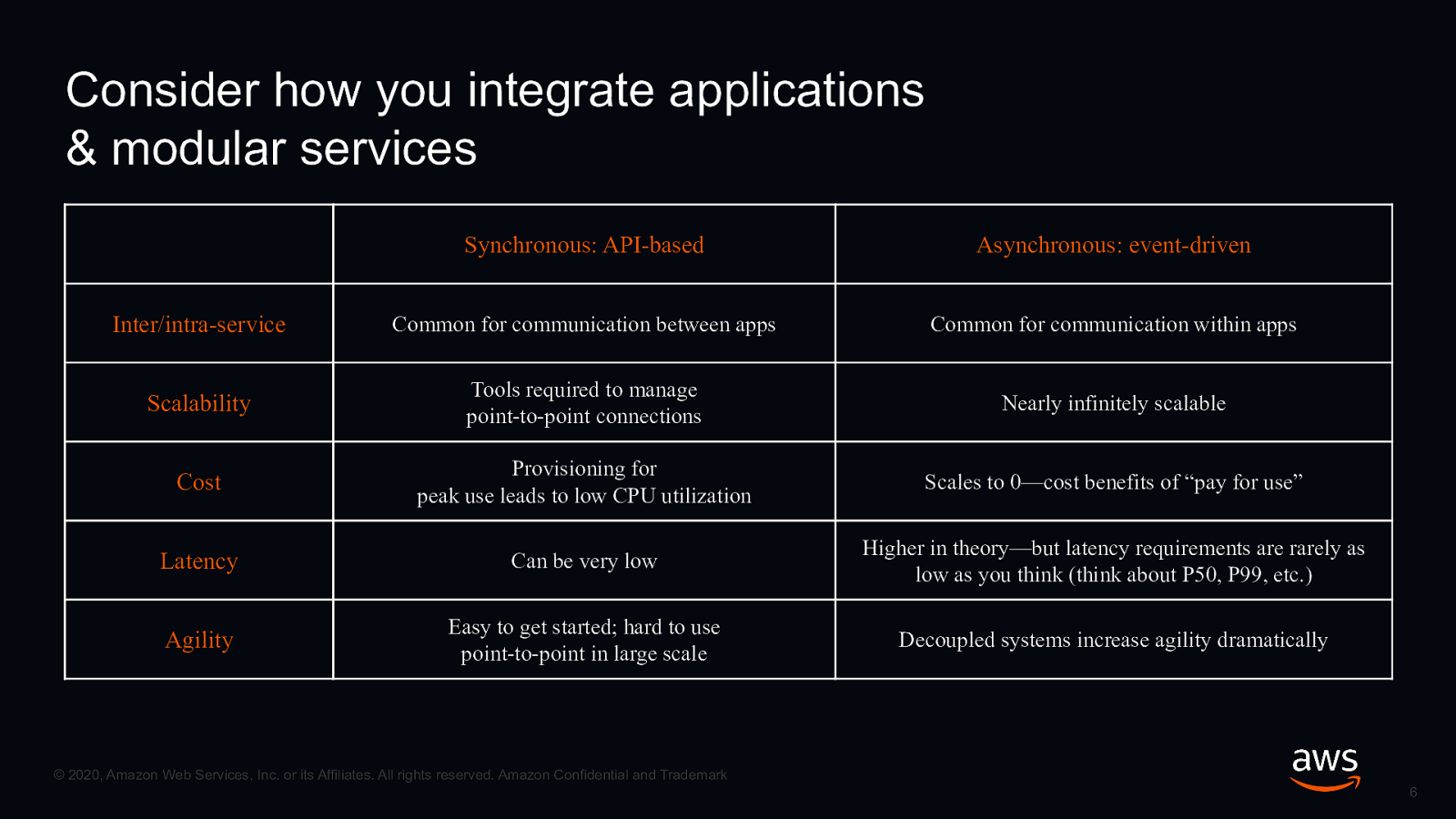
Consider how you integrate applications & modular services Synchronous: API-based Asynchronous: event-driven Inter/intra-service Common for communication between apps Common for communication within apps Scalability Tools required to manage point-to-point connections Nearly infinitely scalable Cost Provisioning for peak use leads to low CPU utilization Scales to 0—cost benefits of “pay for use” Latency Can be very low Higher in theory—but latency requirements are rarely as low as you think (think about P50, P99, etc.) Agility Easy to get started; hard to use point-to-point in large scale Decoupled systems increase agility dramatically © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 6
Slide 7
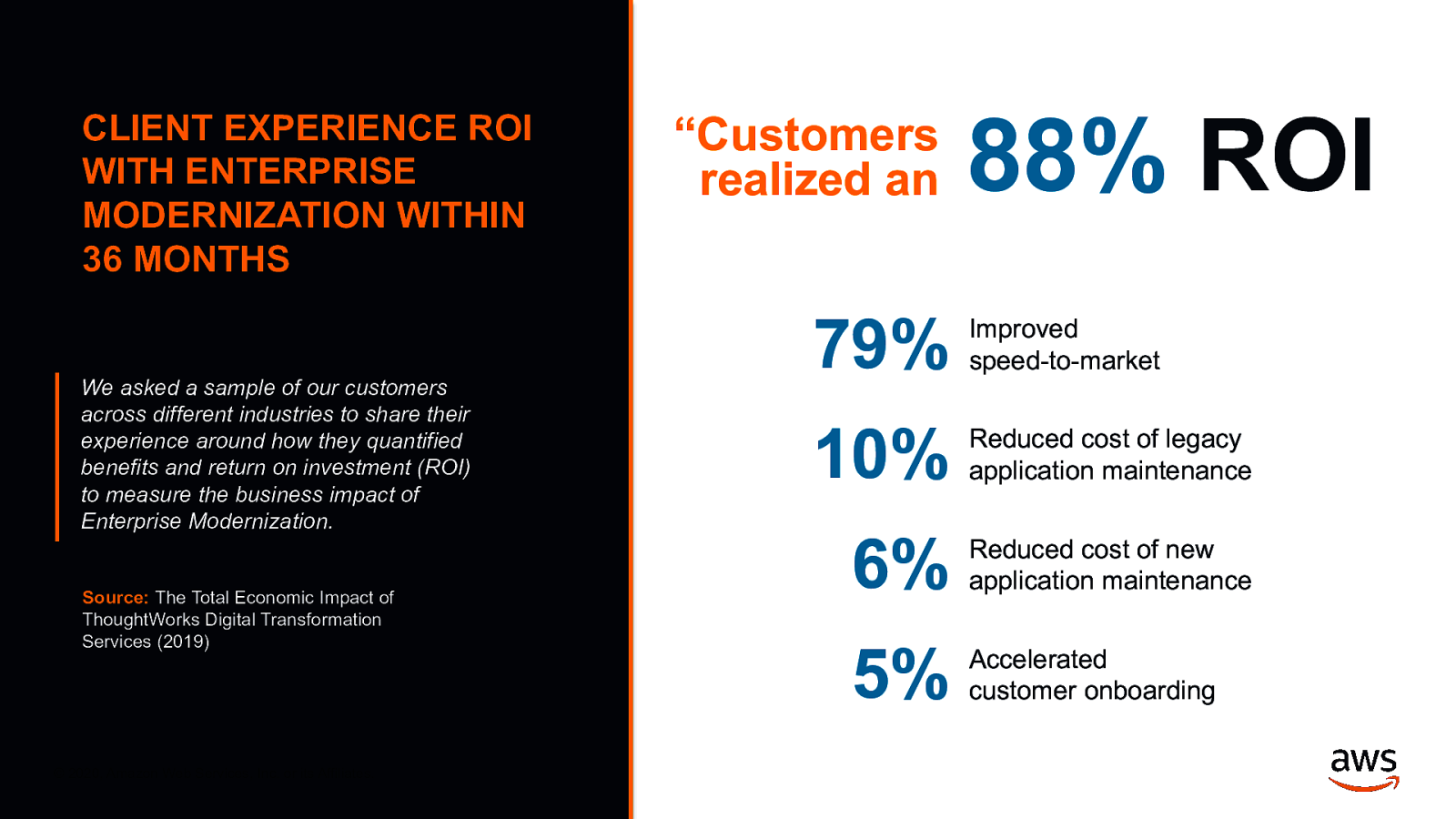
CLIENT EXPERIENCE ROI WITH ENTERPRISE MODERNIZATION WITHIN 36 MONTHS We asked a sample of our customers across different industries to share their experience around how they quantified benefits and return on investment (ROI) to measure the business impact of Enterprise Modernization. Source: The Total Economic Impact of ThoughtWorks Digital Transformation Services (2019) © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. “Customers realized an 88% ROI 79% Improved speed-to-market 10% Reduced cost of legacy application maintenance 6% Reduced cost of new application maintenance 5% Accelerated customer onboarding
Slide 8

Now… Move fast OR AND Stay secure © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 8
Slide 9
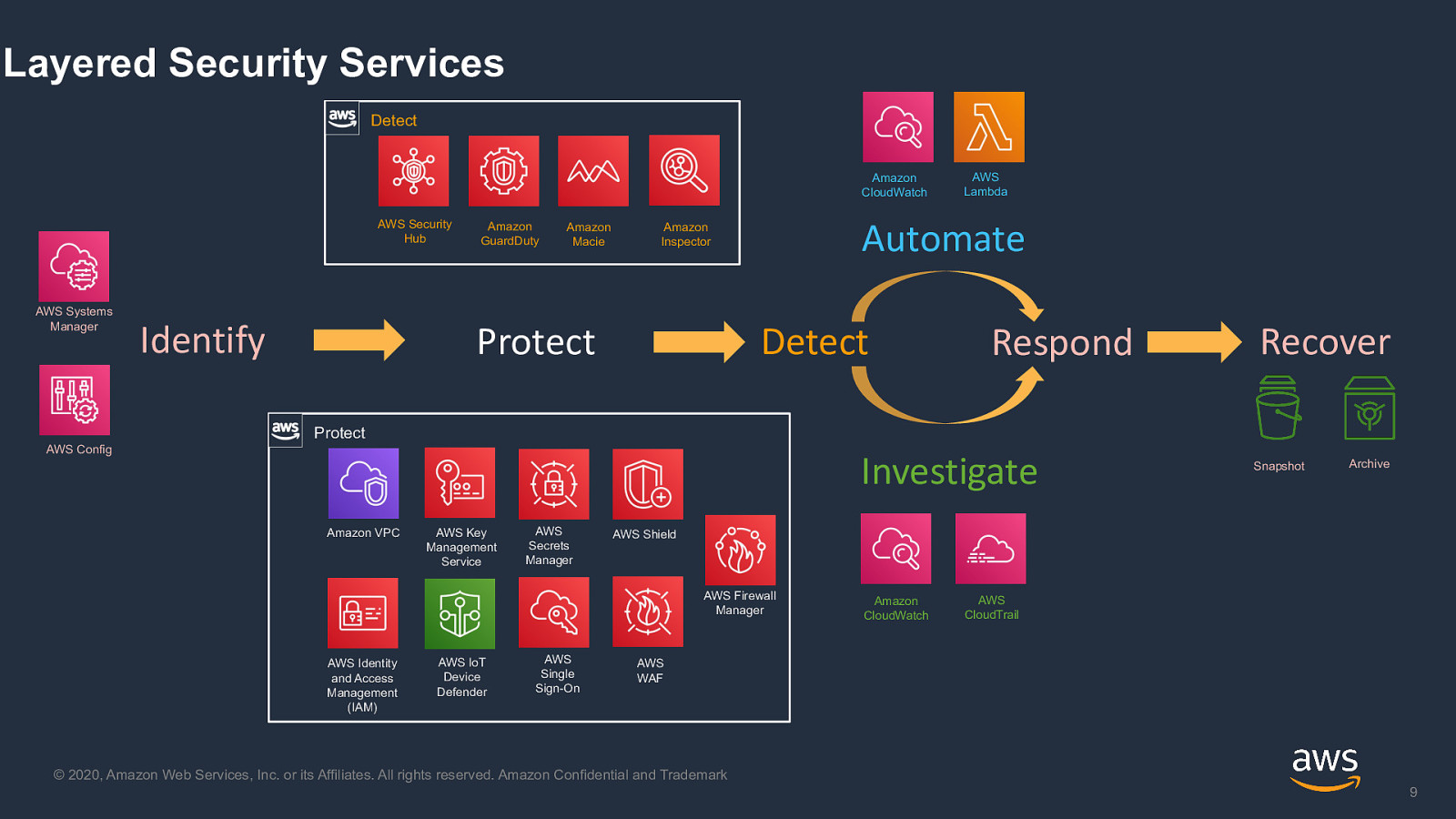
Layered Security Services Detect Amazon CloudWatch AWS Security Hub AWS Systems Manager Identify Amazon GuardDuty Amazon Macie Automate Amazon Inspector Detect Protect AWS Lambda Respond Recover Protect AWS Config Investigate Amazon VPC AWS Key Management Service AWS Secrets Manager AWS IoT Device Defender AWS Single Sign-On Archive AWS Shield AWS Firewall Manager AWS Identity and Access Management (IAM) Snapshot Amazon CloudWatch AWS CloudTrail AWS WAF © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 9
Slide 10
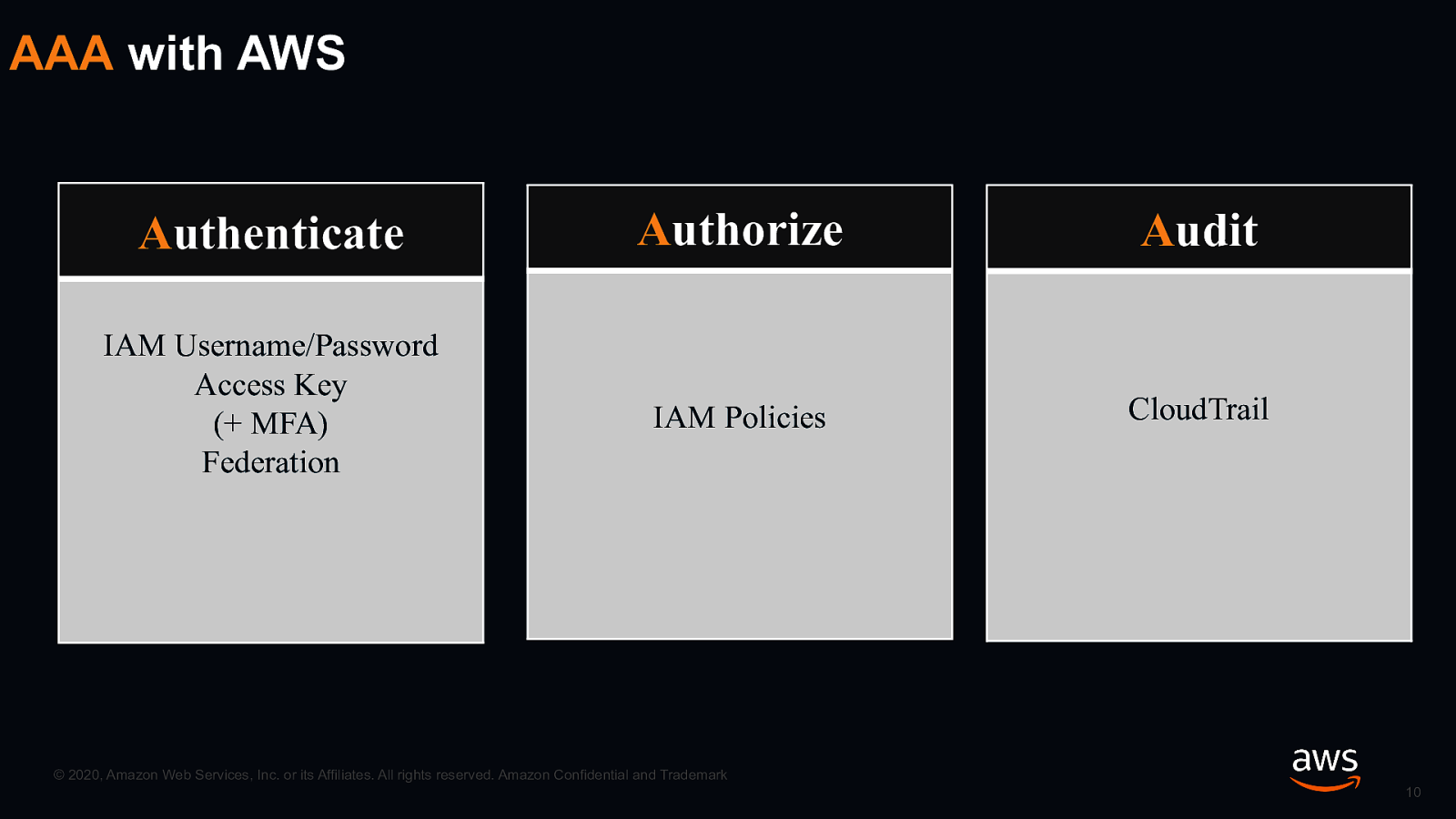
AAA with AWS Authenticate Authorize Audit IAM Username/Password Access Key (+ MFA) Federation IAM Policies CloudTrail © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 10
Slide 11
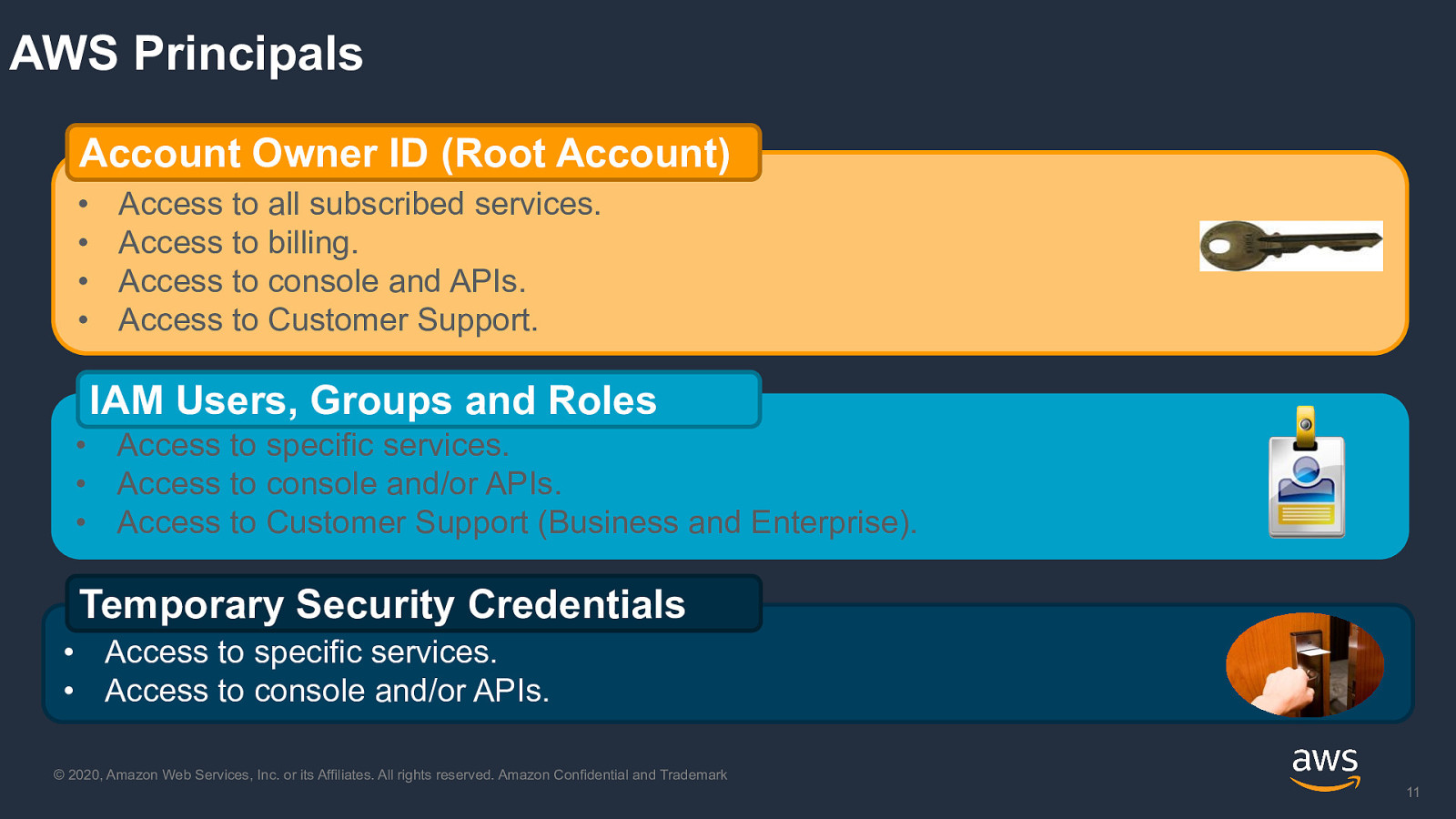
AWS Principals Account Owner ID (Root Account) • • • • Access to all subscribed services. Access to billing. Access to console and APIs. Access to Customer Support. IAM Users, Groups and Roles • Access to specific services. • Access to console and/or APIs. • Access to Customer Support (Business and Enterprise). Temporary Security Credentials • Access to specific services. • Access to console and/or APIs. © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 11
Slide 12

General Best Practices • Clearly define an AWS account-creation process. • Define a company-wide AWS usage policy • Create a security account structure for managing multiple accounts. • Leverage AWS APIs and scripts. © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 12
Slide 13

IAM General Best Practices • • • • • • • • • • • • Lock away your AWS account (root) access keys Create individual IAM users Use groups to assign permissions to IAM users Grant least privilege Configure a strong password policy for your users Enable MFA for privileged users Use roles for applications that run on Amazon EC2 instances Delegate by using roles instead of by sharing credentials Rotate credentials regularly Remove unnecessary credentials Use policy conditions for extra security Monitor activity in your AWS account © 2020, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark 13
Slide 14

SLIs, SLOs, and SLAs
Slide 15

SLIs A Service Level Indicator is a quantitative measurement that expresses an aspect of the service (commonly a metric).
Slide 16

SLOs A Service Level Objective is a target value for a service, as measured via an SLI.
Slide 17

SLAs A Service Level Agreement is a contract that defines the results (and consequences) of meeting (or missing) one or more SLOs.
Slide 18

Business Stakeholders - Product Managers Developers SREs Executives Customers
Slide 19

Data-driven decision making Good data helps you make good decisions by lowering cognitive load, empowering teams to be independent, and unlocking creativity and potential.
Slide 20

Security Posture Management
Slide 21

Security Posture Management Assess and visualize the current and historic security posture of your cloud environment, automate audit evidence collection, and catch configuration issues.
Slide 22

Security Signals Security Signals are generated using Detection Rules. Detection Rules detect threats across different sources and are available out of the box for immediate use.
Slide 23

Demo